Table of Contents
Introduction – Script Injection Vulnerabilities
In the world of cybersecurity, where technology constantly evolves, there’s a lurking threat that often goes unnoticed by the average internet user: script injection vulnerabilities. These vulnerabilities are a playground for cybercriminals, allowing them to inject malicious scripts into web pages that users innocently visit every day. Let’s delve into what these vulnerabilities are, how they work, and what you can do to protect yourself.
What is Script Injection?
Script injection is a technique used by attackers to insert malicious code (typically JavaScript) into web pages viewed by users. This can happen when websites or web applications don’t properly validate or sanitize user inputs, such as form fields, URLs, or cookies. Attackers exploit these weaknesses to inject scripts that can steal sensitive information, hijack sessions, or even distribute malware to unsuspecting visitors.
Real-Life Examples
To grasp the impact of script injection vulnerabilities, let’s look at a couple of real-life examples:
Cross-Site Scripting (XSS) Attacks:
One of the most common types of script injection is Cross-Site Scripting or XSS. In 2020, a major hotel chain fell victim to XSS attacks that exploited a vulnerability in their online booking system. Attackers injected malicious scripts into the website, which then executed in the browsers of users visiting the site. This allowed the attackers to steal customers’ login credentials and credit card information.
Magecart Attacks:
Another infamous example is Magecart attacks, where cybercriminals inject malicious JavaScript into e-commerce websites’ payment pages. This JavaScript captures customers’ payment information, such as credit card details, as they make purchases. Magecart attacks have affected numerous online retailers globally, highlighting the pervasive nature of script injection vulnerabilities.
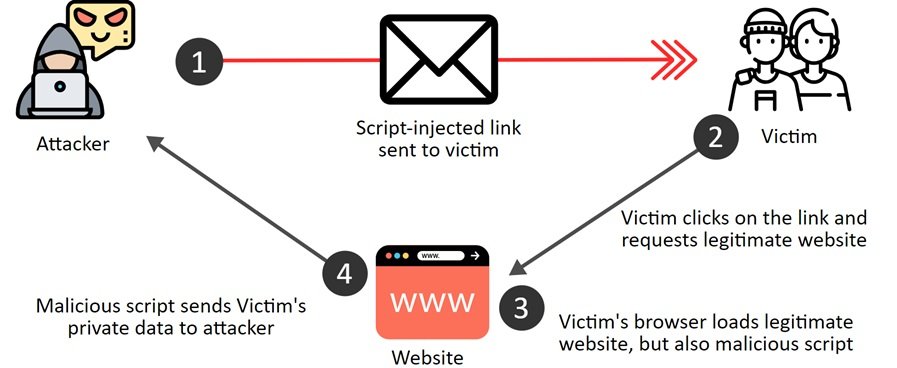
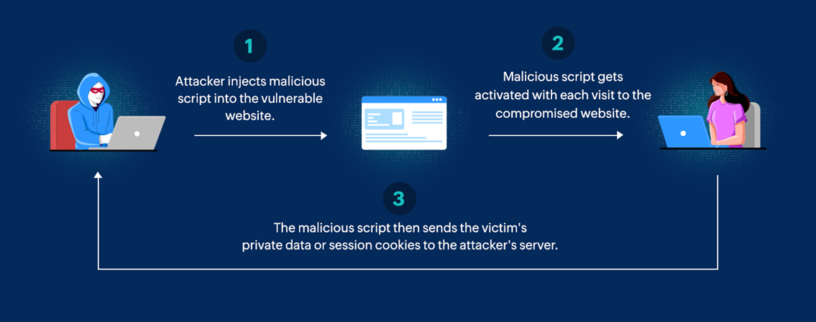
How Script Injection Works
Imagine you’re browsing a reputable website, entering your login details or payment information. Behind the scenes, if the website has a script injection vulnerability, an attacker could have injected malicious code that intercepts and sends your sensitive data to their server. This happens seamlessly and without your knowledge, making script injection a stealthy yet potent threat.
Mitigating the Risk
As a user, you can take steps to protect yourself from script injection vulnerabilities:
- Keep Your Software Updated: Ensure your web browser, antivirus software, and operating system are up to date to mitigate known vulnerabilities.
- Be Wary of Suspicious Links: Avoid clicking on suspicious links or visiting untrusted websites, as these can be sources of script injection attacks.
- Use Browser Security Features: Enable browser security features like Content Security Policy (CSP) and XSS Auditor to mitigate the risks of script injection.
Conclusion
Script injection vulnerabilities pose a significant risk to both individuals and businesses alike. Understanding how these vulnerabilities work and the real-world consequences they can have is crucial in today’s digital landscape. By staying informed and adopting best practices for cybersecurity, you can reduce the chances of falling victim to script injection attacks and protect your online presence effectively.
Remember, vigilance is key when browsing the web. Stay safe, stay informed, and together, we can make the internet a more secure place for everyone.
For more insights on cybersecurity and technology trends, stay tuned to our blog. Don’t forget to share this article with your friends and colleagues to spread awareness about script injection vulnerabilities. Stay secure online!



1 Pingback